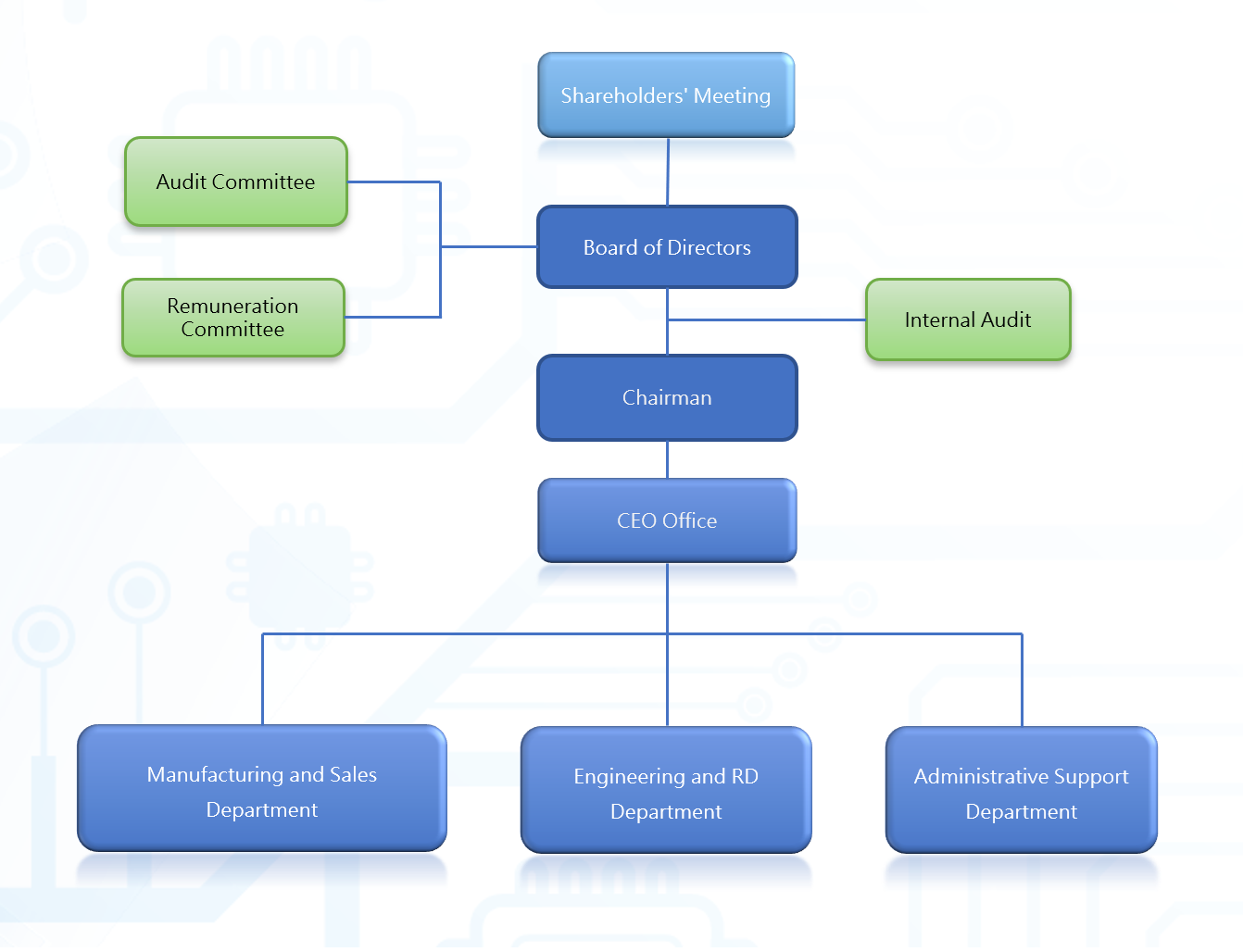
- Company Structure
- Board information
- Functional Committees
- Corporate Integrity Management
- Internal Audit
- Information Security Management Plan
- Intellectual Property Management Plan
- Stakeholders
一、Audit Committee
- The Audit Committee of the company was established on May 22, 2025(Year 114), consisting of 4 members.
- The current term is from May 22, 2025, to May 21, 2028. As of Nov 12, 2025, the committee has held 3 meetings. The attendance of the members is as follows:
Title Name Actual Attendance (B) Proxy Attendance Required Attendance (A) Attendance Rate (B/A) Remarks Independent Director Jiang-Liang Lin 3 0 3 100.00 Convener Independent Director Wei-Chen Wang 3 0 3 100.00 Independent Director Ming-huang Chang 3 0 3 100.00 Independent Director Ya-Ching Yu 3 0 3 100.00 2025/5/22 Newly appointed
Professional Qualifications and Experience of Audit Committee Members
Please refer to the information on board members.
Key Focus Areas of the Audit Committee for the Year
- Establishing or amending the internal control system in accordance with Article 14-1 of the Securities and Exchange Act.
- Assessing the effectiveness of the internal control system.
- Establishing or amending procedures for handling significant financial and business activities, such as the acquisition or disposal of assets, engagement in derivative transactions, lending funds to others, and providing endorsements or guarantees for others, as required by Article 36-1 of the Securities and Exchange Act.
- Matters involving the interests of the directors themselves.
- Major asset or derivative transactions.
- Significant lending, endorsements, or guarantees.
- Raising, issuing, or privately placing equity-related securities.
- Appointment, dismissal, or remuneration of the certifying CPA.
- Appointment or dismissal of financial, accounting, or internal audit officers.
- Annual financial reports signed or stamped by the chairman, manager, and accounting officer, as well as the second-quarter financial reports that require CPA review and certification.
- Other significant matters as stipulated by the company or competent authorities.
The committee held 5 meetings in the most recent year (Year 114). The attendance of the members is as follows:
| Title | Name | Actual Attendance (B) | Proxy Attendance | Required Attendance (A) | Attendance Rate (B/A) | Remarks |
|---|---|---|---|---|---|---|
| Independent Director | Jiang-Liang Lin | 5 | 0 | 5 | 100.00 | Convener |
| Independent Director | Wei-Chen Wang | 5 | 0 | 5 | 100.00 | |
| Independent Director | Ming-huang Chang | 5 | 0 | 5 | 100.00 | |
| Independent Director | Ya-Ching Yu | 3 | 0 | 3 | 100.00 | 2025/5/22 Newly appointed |
二、Remuneration Committee
- The current Compensation Committee was appointed by the Board of Directors on May 22, 2025 (Year 114), and consists of three members.
- The current term is from May 22, 2025, to May 21, 2028. As of Nov 12, 2025, the committee has held 2 meetings. The attendance of the members is as follows:
| Title | Name | Actual Attendance (B) | Proxy Attendance | Required Attendance (A) | Attendance Rate (B/A) | Remarks |
|---|---|---|---|---|---|---|
| Independent Director | Wei-Chen Wang | 2 | 0 | 2 | 100.00 | Convener |
| Independent Director | Jiang-Liang Lin | 2 | 0 | 2 | 100.00 | |
| Independent Director | Ming-huang Chang | 2 | 0 | 2 | 100.00 |
Responsibilities of the Compensation Committee
- Establish and Regularly Review the performance evaluation standards for the company's directors and managers, as well as the annual and long-term performance goals, policies, systems, standards, and structures for compensation and remuneration. The performance evaluation standards should be disclosed in the company's annual report.
- Regularly Assess the achievement of performance goals by the company's directors and managers. Based on the results of these performance evaluations, the committee will determine the specific content and amounts of individual compensation and remuneration. The annual report should disclose the individual performance evaluation results, the content and amounts of individual compensation, and the relationship and reasonableness between the remuneration and performance evaluation results. This information should also be reported at the shareholders' meeting.
The committee held 4 meetings in the most recent year (Year 114). The attendance of the members is as follows:
| Title | Name | Actual Attendance (B) | Proxy Attendance | Required Attendance (A) | Attendance Rate (B/A) | Remarks |
|---|---|---|---|---|---|---|
| Independent Director | Wei-Chen Wang | 4 | 0 | 4 | 100.00 | Convener |
| Independent Director | Jiang-Liang Lin | 4 | 0 | 4 | 100.00 | |
| Independent Director | Ming-huang Chang | 4 | 0 | 4 | 100.00 |
三、Sustainability Committee
- The current Sustainable Development Committee was appointed by the Board of Directors on Aug 05, 2025 (Year 114), and consists of three members.
- The current term is from Aug 05, 2025, to May 21, 2028. As of Oct. 28, 2025, the committee has held 1 meetings. The attendance of the members is as follows:
| Title | Name | Actual Attendance (B) | Proxy Attendance | Required Attendance (A) | Attendance Rate (B/A) | Remarks |
|---|---|---|---|---|---|---|
| Director | Te-Hsun Huang | 1 | 0 | 1 | 100.00 | Convener |
| Director | Tseng-Wen Chen | 1 | 0 | 1 | 100.00 | |
| Committee | Yu-Lin Lan | 1 | 0 | 1 | 100.00 |
Responsibilities of the Compensation Committee
- Establish, promote, and strengthen the company's sustainable development policies, annual plans, and strategies.
- Review, track, and revise the implementation status and effectiveness of sustainable development.
- Supervise sustainability-related disclosures and review the Sustainability Report.
- Oversee the execution of the Company’s Sustainability Development Code and other sustainability-related tasks as resolved by the Board of Directors.
Communication Between Independent Directors, the Head of Internal Audit, and External Auditors
I. The Company’s Audit Committee is composed entirely of independent directors and convenes at least once per quarter, with additional meetings held as necessary.
II. One-on-One Communication Between the Head of Internal Audit and the Audit Committee:
- Regular communication – The Head of Internal Audit reports audit findings and the status of corrective actions to the Audit Committee, responds to inquiries raised by independent directors, and enhances audit scope and focus in accordance with their guidance to ensure the effectiveness of the internal control system.
- Ad hoc communication – Audit findings and initiatives to continuously enhance audit value are communicated through telephone calls, emails, or in-person meetings as needed. Any material non-compliance issues are reported to the independent directors immediately.
- Summary of major communications in 2025:
Date |
Meeting |
Key Discussion Items |
Outcomes |
2025/02/17 |
Audit Committee |
1. Report on the execution status of the audit plan for October–December 2024. 2. Report on the Statement on Internal Control for 2025. 3. Amendments to the Company’s internal control system. |
Approved by the Audit Committee and submitted to the Board of Directors. |
2025/02/17 |
Internal Audit Meeting |
1. Internal audit operations report. 2. Review of audit reports by independent directors. |
Approved and submitted to the Board of Directors. |
2025/05/12 |
Audit Committee |
Report on the execution status of the audit plan for January–March 2025. |
No objections were raised. |
2025/08/05 |
Audit Committee |
Report on the execution status of the audit plan for April–June 2025. |
No objections were raised. |
2025/09/26 |
Audit Committee |
Proposed disposal of real estate assets. |
Approved by the Audit Committee and submitted to the Board of Directors. |
2025/11/12 |
Audit Committee |
1. Report on the execution status of the audit plan for July–September 2025. 2. Amendments to the Company’s internal control system. 3. Proposal of the internal audit plan for 2026. |
Approved by the Audit Committee and submitted to the Board of Directors. |
III. One-on-One Communication Between External Auditors and the Audit Committee:
- Regular communication – External auditors communicate with the Audit Committee regarding audit plans, execution status, and audit results before and after the issuance of the annual report.
- Ad hoc communication – Meetings are arranged as needed to discuss other operational, internal control, or related matters requiring timely communication.
- Summary of major communications in 2025:
Date |
Meeting |
Key Discussion Items |
Outcomes |
2025/02/17 |
Audit Committee |
Financial statements for fiscal year 2024. |
No objections were raised. |
2025/02/17 |
(Auditors’ Private Session with Independent Directors) |
1. Audit plan for fiscal year 2025. 2. Financial statements for fiscal year 2024. 3. Review of audit reports by independent directors. |
No objections were raised. |
2025/05/12 |
Audit Committee |
First-quarter financial statements for fiscal year 2025. |
No objections were raised. |
2025/08/05 |
Audit Committee |
Second-quarter financial statements for fiscal year 2025. |
No objections were raised. |
2025/09/26 |
Audit Committee |
Proposed disposal of real estate assets. |
No objections were raised. |
2025/11/12 |
Audit Committee |
Third-quarter financial statements for fiscal year 2025. |
No objections were raised. |
Policy and Guidelines
In adherence to the principles of fairness and honesty, our company conducts business activities guided by a comprehensive framework to uphold integrity. This framework includes the Code of Ethical Conduct, Procedures for Ethical Business Practices and Guidelines for Conduct, and Standards of Ethical Behavior, all approved by the Board of Directors. The Sustainability Development Committee oversees implementation, reporting to the Board at least annually. The most recent report was presented on November 12, 2025.
Preventive Measures
Prevention of Insider Trading
Our company has established mechanisms for the disclosure and management of significant information through the Insider Trading Prevention Operational Procedures, accessible to employees via the internal "DCC Information Center." These measures ensure compliance and prevent occurrences of insider trading.
Integrity Clauses
Employees sign an employment agreement upon hiring, which includes provisions for the protection and appropriate use of confidential information within their job scope. These confidentiality obligations extend beyond employment. Additionally, relevant documents, including the Code of Ethical Conduct, are disclosed on the company website. Suppliers are required to sign a Supplier Integrity Commitment.
Conflict of Interest Avoidance
The company's Board of Directors Meeting Rules include a conflict of interest avoidance policy. Directors must disclose any personal interest related to agenda items during board meetings. If such interests may harm the company, directors can express opinions but must abstain from discussion and voting, and cannot represent others in such matters. This policy has been fully implemented, with related abstentions documented in meeting minutes.
Regular Internal Training
Annual training sessions reinforce employees' understanding and application of core values related to integrity management. Topics include corporate social responsibility, professional ethics, protection of confidential information, and intellectual property rights. These initiatives enhance legal awareness and ethical standards among all employees.
Whistleblowing Mechanism
To ensure comprehensive implementation of ethical practices, a complaint mailbox (檢舉制度4.3) is available for internal and external stakeholders to report any violations of integrity. All reports are handled confidentially by designated units, investigated thoroughly, and, if verified, addressed with appropriate action.
Implementation Overview
1. The Company regularly communicates its integrity and ethical management policies to employees, reinforcing integrity-based core values and business principles.
2. All newly hired employees are required to sign employment contracts that include integrity and ethical management clauses and to complete onboarding training. The compliance rate reached 100%.
3. All directors and senior management have signed statements of integrity and ethical management, achieving a 100% signing rate.
4. All employees have signed the “Integrity Commitment Statement,” with a 100% signing rate.
5. Key suppliers, customers, and contractual counterparties are required to sign an “Integrity and Anti-Corruption Statement.” A cumulative total of 10 statements have been signed.
6. During the year, the Board of Directors effectively implemented conflict-of-interest avoidance mechanisms.
7. During the year, the Company received zero reported cases through its integrity and ethical conduct reporting mailbox.
8. The Company conducted internal training programs on regulations related to ethical management, prevention of insider trading, information security, and protection of trade secrets. A total of 54 participant attendances were recorded, with an aggregate of 79.5 training hours.
1. Ethical Corporate Management Best Practice Principles | |
2. Procedures for Ethical Management and Guidelines for Conduct | |
3. Codes of Ethical Conduct | |
4. Ethical Corporate Summy Checklist |
Purpose of Internal Audit
The purpose of conducting internal audits is to assess the effectiveness, efficiency, and compliance of the company's policies and procedures, assist the board of directors and management in evaluating internal control systems, identify deficiencies and imbalances, and provide recommendations for improvement. This ensures that the internal control system remains effective and serves as a basis for revising internal control measures.
Internal Audit Organization
The internal audit unit of our company reports directly to the board of directors and is staffed by an audit supervisor and personnel approved by the audit committee and the board of directors.
Operation of Internal Audits
Audit Scope
The scope of audits covers all operations of the company and its subsidiaries.
Audit Methods
Audit work focuses on evaluating the effectiveness of internal controls for various business activities and assessing the quality of risk management and control. Regular audits and unscheduled audits are conducted as needed.
Each year, the company prepares an audit plan based on the risk assessment results of various activities, specifying the scope and frequency of audits. The audit findings and recommendations for improvements are reported to the audit committee and the board of directors, serving as a basis for improving the internal control system.
Audit Reports
Except for reports approved by the audit committee, the audit supervisor also reports periodically to the audit committee and the board of directors on the progress and results of the audit.
I. Information Security Management Strategy and Structure
(1) Information Security Risk Management Structure
1. Information Security Governance Organization
The company’s dedicated information security unit is managed by the Information Department, currently with a Chief Information Security Officer (CISO) (held concurrently by the General Manager), one Information Security manager and one security personnel. They are responsible for the formulation, implementation, risk management, and compliance of information security policies, with regular reviews and adjustments. The Audit Office conducts annual audits of the information security management operations and reports the results to the Board of Directors and the Audit Committee.
2. Information Security Organizational Structure
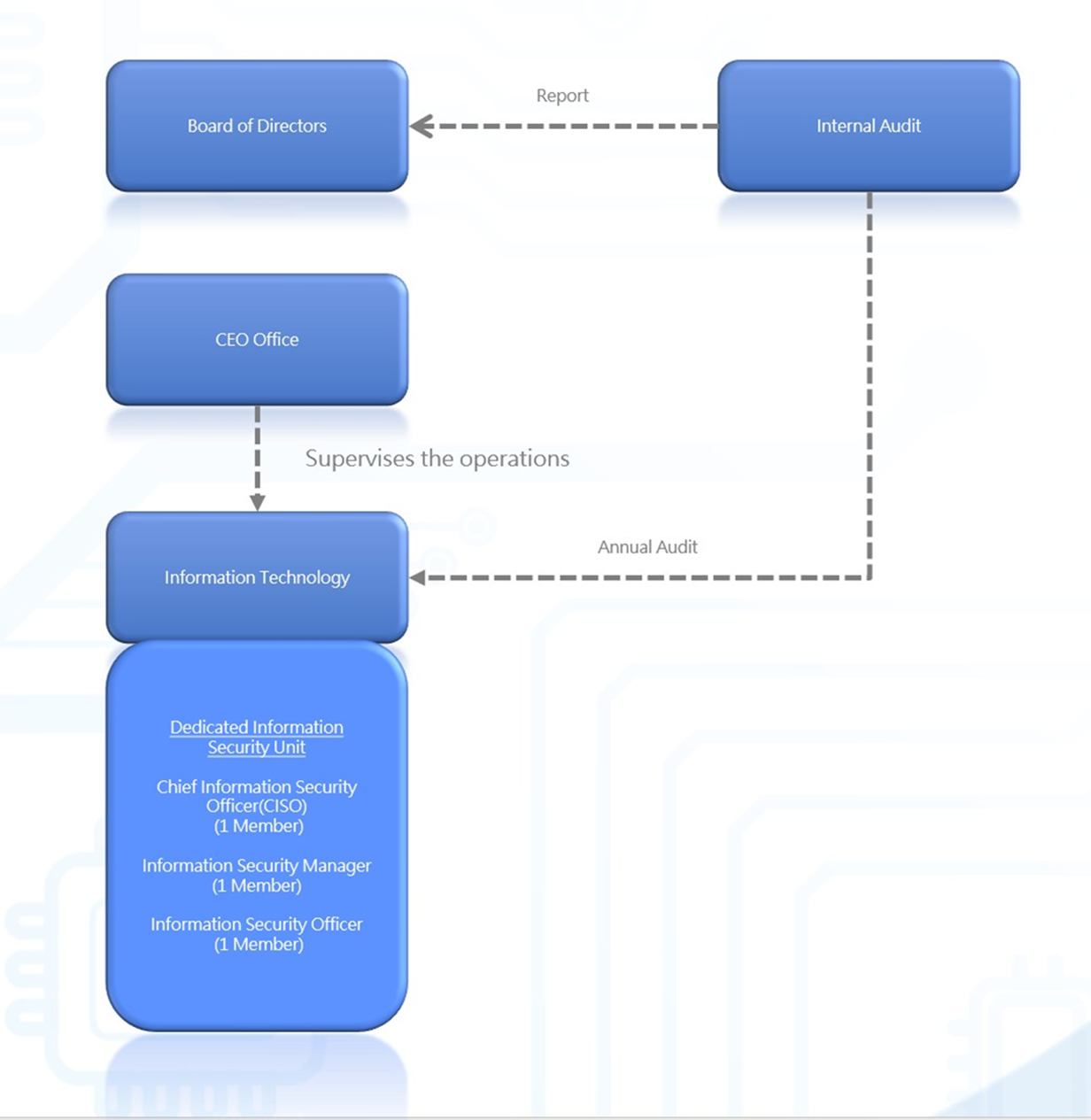
(2) Information Security Policies
The company has established operational procedures such as "Information Management Procedures", "Information System Access Control Procedures", "Data Backup Management Procedures", and "Information Security Inspection Procedures".
(1) Establish monitoring and control mechanisms for information assets, with all personnel having the responsibility and obligation to protect their respective information assets, ensuring the confidentiality, integrity, and availability of the company’s critical information assets.
(2) Job responsibilities should be appropriately segregated, and only the necessary permissions and information required for job completion should be granted.
(3) Necessary assessments should be conducted when hiring personnel, and relevant operational guidelines should be signed to ensure that maintaining information security is an obligation embedded in daily work.
(4) Establish a business continuity management mechanism to maintain its applicability.
(5) The company’s information security measures must comply with legal regulations and the company’s information security-related procedures; the establishment and modification of all information security standards or procedures must adhere to the mechanisms of the information security management system.
1. Specific Management Plans:
Information security management measures are explained as follows:
(1) Regulatory Compliance: The company has established several internal information security standards and procedures to regulate the information security behaviors of personnel, regularly reviewing relevant systems to ensure compliance with operational changes and adjusting as needed.
(2) System Protection: To prevent various internal/external information security threats, in addition to network architecture design, the company has also implemented firewall and endpoint protection software to enhance the overall security of the information environment.
(3) Personnel Training: The company regularly promotes information security issues to enhance employees’ information security knowledge and professional skills.
Specific Practices:
| Item | Specific Management Plan |
|
Network Control |
Restrict access to the company’s network to only company devices and wired network access points. The firewall restricts access to VPN resources; wireless networks provide only internet services, prohibiting the use of wireless networks to connect to internal company resources. |
|
System Access Control |
Systems include ERP, Run Portal, E-Mail, VPN, etc. For new employees, the management department fills out the "New and Change Information System Account and Access Control Application Form," and the Information Engineering unit creates accounts and sets default permissions. Upon employee resignation, the Information Engineering unit deletes or disables the employee’s account according to the "Resignation Management Procedures." The Information unit also periodically provides access lists to supervisors to review the appropriateness of their subordinates’ access rights. |
|
Data Backup and Restoration |
Regularly back up important file data; the file server automatically synchronizes with the file synchronization server and off-site file server in real-time. |
|
Virus Protection |
The firewall has built-in virus engines/WAN control, and computers are equipped with endpoint protection software. |
|
Data Leakage Prevention |
During the product development process, output data at each stage is reviewed by the supervising unit and transferred to the Document Control Center (DCC) for filing. If product development documents are needed for reference or borrowing, a "Product Development Document Borrowing and Copying Application Form" must be filled out and approved by the authorized supervisor before borrowing and copying. Critical R&D data is stored on the company’s file server, located behind the firewall, with access controls in place, granting read-only access to approved applicants. |
Review and Continuous Improvement
| Item | Specific Management Plan |
|
Education and Training Promotion |
Information security issues and recent events are periodically promoted to all employees via internal emails. New employees must complete the "Information System and Information Security Introduction Course" to ensure they understand the company’s information security policies. |
2. Resources Invested in Information Security Management
The company regularly reviews the overall information security planning to reflect the current situation and strengthens the promotion of information security concepts among employees. In addition, the company regularly inspects and maintains host equipment and firewalls, incorporating computer information system-related control operations into the annual audit plan.
In 2025, the Company’s Chief Information Security Officer (CISO) and information security personnel participated in a total of eight cybersecurity seminars and training programs as part of the Company’s ongoing efforts to strengthen information security governance and risk management.
II. Information Security Risks and Mitigation Measures
The company has established information security protection measures, but it cannot guarantee complete avoidance of cyber-attacks. Continuous improvements to information security standards are necessary to keep up with evolving threats.
III. Major Information Security Incidents
In the past year and up to the date of the annual report, the company has not experienced any major information security incidents. However, with the increasing threats to information security, the requirements and tools for information security will need to evolve accordingly.
IV. Board Reporting Date
November 12, 2025
Intellectual Property Management Vision
Our company places a high emphasis on compliance with laws and the protection of intellectual property rights. Understanding the importance of laws and intellectual property to enterprises, we established the Legal and Intellectual Property Department at the inception of our company. This department integrates legal resources with intellectual property management to identify legal risks related to intellectual property, achieving a comprehensive risk management mechanism that includes "planning, prevention, management, execution, obstruction, and perfection." Our company does not proactively use legal actions as a tool for business competition but instead strengthens legal measures and emphasizes preemptive prevention as a means of defense against disputes. We have established a comprehensive intellectual property management system to rigorously protect our advanced and critical technologies developed through the dedication of our research and development personnel, and to defend against competitors' attempts to use intellectual property litigation as a means of achieving business competition objectives, thereby reducing the risk of operational infringement and achieving a strategy of sustainable operation.
Basic Policies for Intellectual Property Management
Our company combines the basic policy of intellectual property rights with the company's business goals and research and development resources, ensuring that our core technologies, innovative inventions, research and development works, know-how, trademarks, and trade secrets are well protected and that the relevant rights of others are not infringed.
Intellectual Property Management System
1. Patent Rights and Integrated Circuit Layout Protection
- Our company has established the "Patent Proposal Incentive Plan," setting up a mechanism for patent review committees that clearly stipulates the classification of ideas/technologies, the patent application process, the determination of application categories and countries, the agreement on patent ownership, and the obligations of patent inventors. All patent proposals must be reviewed by the patent review committee, supplemented by a hierarchical evaluation process to distinguish between those that will be treated as trade secrets or filed for patent applications based on the importance and nature of the technology. At the same time, we have set up a reward system for employee patent proposals and granted patents to enhance and adequately protect our patent assets in terms of both quality and quantity.
- We have established a complete patent management system to manage patent-related information and the payment of maintenance fees, and to conduct annual reviews of patent rights.
- We regularly review patent assets and effectively combine existing patent assets with our company's projects or products to enhance the market competitiveness and economic value of our products.
- We actively engage in strategic collaborations with other companies, using existing patent rights to develop customized products for customers or for cross-licensing, thereby maximizing the use of patent assets and achieving a win-win situation between our company and others.
- Before developing new products, we conduct patent searches, design patent maps, and regularly monitor competitors' patent technologies to provide references for our R&D personnel in developing innovative products, thereby avoiding infringement and respecting third-party intellectual property rights while reducing the waste of our company's R&D resources.
- We have established important circuit layout output and protection policies that regulate the qualifications, applications, levels, permissions, and methods of access personnel.
- Our R&D personnel regularly engage in brainstorming sessions and idea excavation to inspire infinite possibilities of innovative technologies and enhance the quality of patent proposals.
- We conduct regular internal patent education and training, explaining patent laws, promoting patent application procedures, and discussing practical cases.
2. Trade Secret Protection
- We have formulated various document and data control procedures, specifying the classification and control regulations for all internal and external documents and data.
- We have established computer file management, network, and information security control procedures to ensure the confidentiality, integrity, security, and availability of all intangible assets, information, and trade secrets. Important drawings, software programs, electronic documents, etc., must be strictly encrypted and stored.
- We have established personal data protection management methods to ensure the correct use and storage of internal and external personal data.
- We have established physical access control and important entrance and exit controls, along with security measures to adequately protect the company's trade secrets.
- New employees undergo orientation training and sign employment contracts upon joining, informing them not to bring trade secrets from previous employers to our company. They must only use confidential information created and known during their employment within their job scope. Employees agree to comply with the employee code of conduct, in-service confidentiality obligations, loyalty obligations, and post-employment confidentiality obligations, and are prohibited from disclosing any company confidential information to third parties without prior written consent from the company.
- Employees involved in major confidential projects during their employment must also sign specific confidentiality agreements.
- We sign confidentiality agreements with customers, suppliers, and agents to adequately protect the trade secrets of both parties.
3. Trademark Protection
- To enable third parties to distinguish the source and representation of goods or services, our company applied for trademarks in multiple countries at the time of its establishment, actively obtaining trademark rights for the company's and its affiliates' business names and product representations. Through trademark rights, we build the company's reputation, guide market trust, and further create the company's brand value.
- Trademark rights are the soul of a well-managed company. Applying for and registering trademarks can obtain exclusive trademark rights protected by law, effectively preventing third parties from registering identical or similar trademarks on identical or similar goods or services.
- We regularly manage and review the trademark register, handling trademark renewals and usage declarations according to deadlines to ensure the validity of trademarks.
- We effectively exercise trademark rights by marking approved trademark designs on software, documents, products, packaging, and various related items to enhance trademark distinctiveness and prevent improper infringement, thereby reducing damage to the company's reputation.
- We track trademark status quarterly and search for similar trademarks to prevent infringement of the company's trademark rights.
- In contracts with partners, we clearly define the scope, duration, and marking methods of trademark licensing to ensure legal and reasonable use of trademarks.
4. Copyright Protection
- In the employment contracts of new employees, we clearly stipulate that "the copyright of works produced on duty" or "the copyright of works produced using company resources" belongs to the company to protect the company's copyrights.
- We implement policies for R&D logs/notes, recording and properly preserving ideas or technologies produced by internal R&D personnel during the innovation and development process.
- We designate specific custodians and encrypt/lock important R&D-related documents or disks.
- We regulate the use of company computers and the installation/uninstallation of software, all controlled by the IT department to prevent copyright infringement or being infringed.
- We clearly stipulate copyright ownership with customers, suppliers, and agents and require partners to guarantee that they do not infringe on the intellectual property rights of others.
Implementation
In response to the intellectual property management plan, our company revises related management methods in real-time to comply with updated regulations and regularly reviews implementation status:
1. Patent Rights and Integrated Circuit Layout Protection
- Our company summarizes and reports the management and implementation results of intellectual property rights to the Board of Directors once a year. The report date for the Board of Directors is as follows: November 12, 2025.
- As of October 31, 2025, our company has accumulated 109 approved patents worldwide, distributed in Taiwan, China, the United States, and other regions, with 3 patents pending.
- We conduct prior art searches for our company's R&D innovation projects, strengthen patent layouts, assist R&D teams in design avoidance, and obtain patent rights to create competitiveness and economic value for company products.
- We regularly maintain patents and review their applicability to company products or projects, while also creating patent maps and R&D flowcharts that align with the company's business goals.
2. Trade Secret Protection
- We regularly collaborate with the IT department to promote trade secret protection and conduct employee computer inspections, strengthening trade secret and information security management.
- We regularly collaborate with the R&D department to inspect R&D logs/notes, properly protecting the trade secrets of important core technologies.
- We regularly inventory and establish management lists for the scope of trade secrets.
- We establish a cross-protection mechanism for patents and trade secrets.
- We strengthen external confidentiality measures and specify confidentiality obligations and scopes in confidentiality agreements.
- We set up account passwords for personal computers and enforce regular password updates. Appropriate firewall equipment is installed to block malicious external attacks.
- We implement access control, setting permissions for employee access cards based on job nature. Visitors must register their identities when entering the company, and unauthorized access to the warehouse is prohibited.
- We regularly conduct educational training on trade secret protection and supervise its implementation in the workplace environment.
3. Trademark Protection
- As of October 31, 2025, our company has obtained 18 approved trademark rights worldwide.
4. Copyright Protection
- To avoid copyright infringement, all software installation permissions are managed uniformly by the IT department.
Pursuing sustainable development, the company establishes transparent and effective multi-directional communication channels with all stakeholders to understand their needs and expectations for Fintek. This serves as an important reference for developing business strategies, CSR policies, and related plans.
Stakeholders are defined as individuals or groups who affect or are affected by the company. Based on this definition, we have identified four main stakeholder categories: investors, employees, customers, and suppliers.
| Stakeholder | Issues of Concern | Communication Channels & Frequency | Contact Window | 2024/09 Communication Outcomes |
|---|---|---|---|---|
| Shareholders and Investors | Business and financial information Corporate governance Shareholder rights Regulatory compliance |
*Market Observation Post System (as required) *Investor conferences (irregular) *Investor email contact *Annual shareholders’ meeting |
Spokesperson: VP Kris Chen Tel: (03)5600-168 Email: kris_chen@fintek.com.tw Stock Agent: Mega Securities Co., Ltd. Address: 1F, No. 95, Sec. 2, Zhongxiao E. Rd., Taipei Tel: (02)3393-0898 |
*Shareholder meeting attendance rate: 56.77% *Investor section and contact info available on company website; all inquiries are directed to appropriate personnel for prompt handling |
| Employees | Employee benefits Career development Regulatory compliance Occupational safety and health Labor relations |
*Welfare announcements (irregular) *Training sessions (irregular) *Performance evaluations (biannually) *Labor-management meetings (quarterly) |
HR Department Tel: (03)5600-168 Email: hr@fintek.com.tw |
*4 birthday events, 8 travel info posts *Onboarding and professional training *Performance reviews twice a year *4 labor-management meetings |
| Customers | Product quality and delivery Customer service Product showcases |
*Service hotline and email *Annual customer satisfaction survey *Real-time updates on product software via official website *Dealer meetings (twice/month) |
Customer Service Tel: (02)8227-8027 Email: sales@fintek.com.tw |
*One customer satisfaction survey with average score of 9.1/10; all issues resolved *27 complaints received and resolved |
| Suppliers | Supplier management Business integrity |
*Two-way communication *Supplier evaluation (regular) *Annual audits of each contractor |
Product Quality Tel: (03)5600-168 Email: qa@fintek.com.tw |
*4 contractor audits conducted |
| Government / Regulatory Agencies | Regulatory compliance Financial performance Information security Waste management Labor relations |
*Government policy briefings (irregular) *Market Observation Post System (irregular) *Company website (irregular) *Official document correspondence (irregular) |
Spokesperson: VP Kris Chen Tel: (03)5600-168 Email: kris_chen@fintek.com.tw |
*All required disclosures made in accordance with regulations *Official letters from authorities (e.g. Ministry of Labor, MOEA, Tax Bureau) are forwarded to responsible departments for processing |
The stakeholder concerns and communication outcomes are compiled and reported to the Board of Directors once annually. The latest report was submitted on November 7, 2024.
Month | Monthly | Same Month Last Year | YoY | YTD | Previous YTD | YoY |
|---|---|---|---|---|---|---|
Jan. | 43,461 | 39,635 | 9.65% | 43,461 | 39,635 | 9.65% |
Feb. | 39,084 | 36,461 | 7.19% | 82,545 | 76,096 | 8.47% |
Mar. | 42,047 | 40,898 | 2.81% | 124,592 | 116,994 | 6.49% |
Apr. | 44,253 | 45,793 | -3.36% | 168,845 | 162,787 | 3.72% |
May. | 46,834 | 44,905 | 4.30% | 215,679 | 207,692 | 3.85% |
Jun. | 46,962 | 45,670 | 2.83% | 262,641 | 253,362 | 3.66% |
Jul. | 49,838 | 44,079 | 13.07% | 312,479 | 297,441 | 5.06% |
Aug. | 47,305 | 44,360 | 6.64% | 359,784 | 341,801 | 5.26% |
Sep. | 47,042 | 45,033 | 4.46% | 406,826 | 386,834 | 5.17% |
Oct. | 45,240 | 44,806 | 0.97% | 452,066 | 431,640 | 4.73% |
Nov. | 44,815 | 41,136 | 8.94% | 496,881 | 472,776 | 5.10% |

MEGA Securities Co., Ltd. Shareholder Services Department
TEL:+886-2-33930898

Company Spokesperson
Kris Chen
Phone No.:+886-3-560-0168
kris_chen@fintek.com.tw

